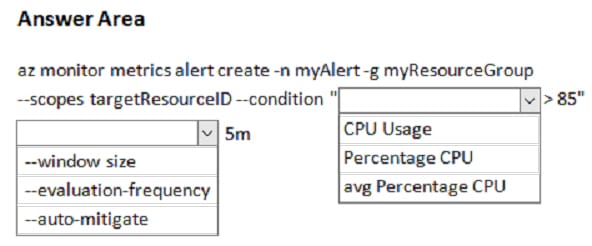
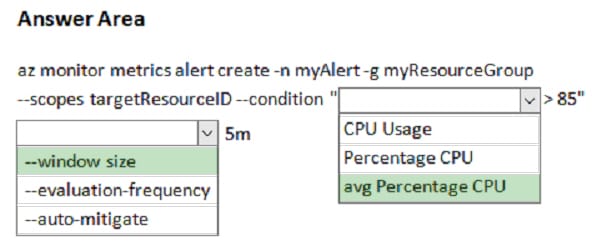
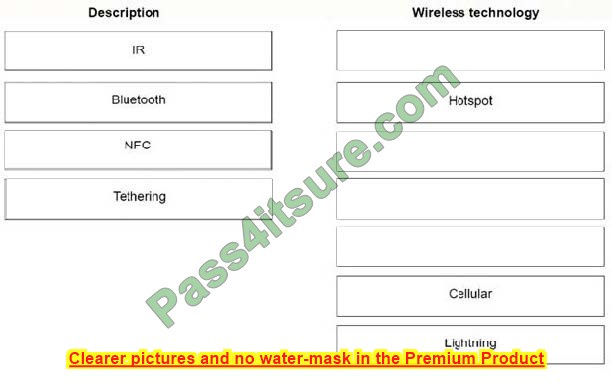
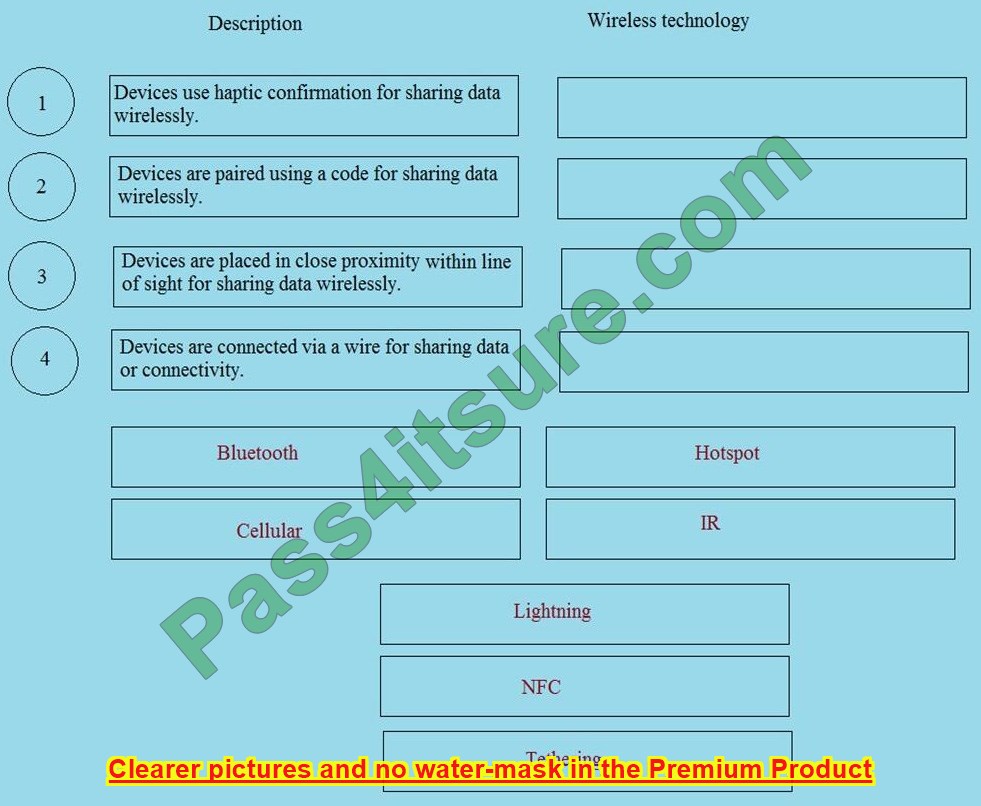
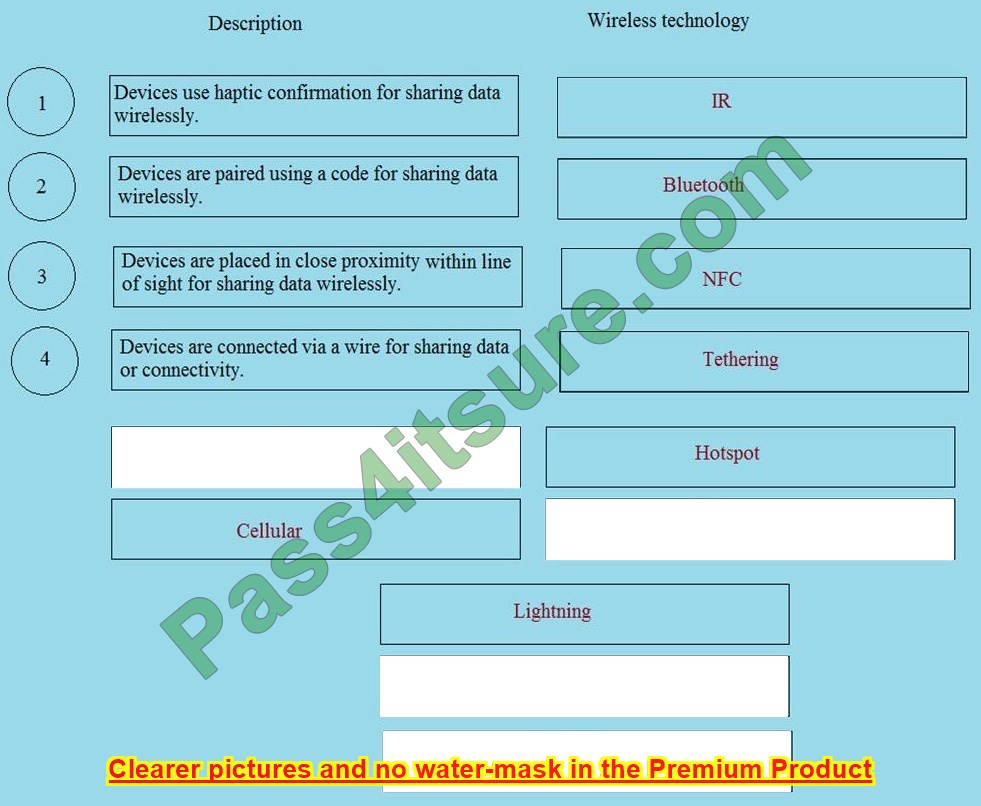
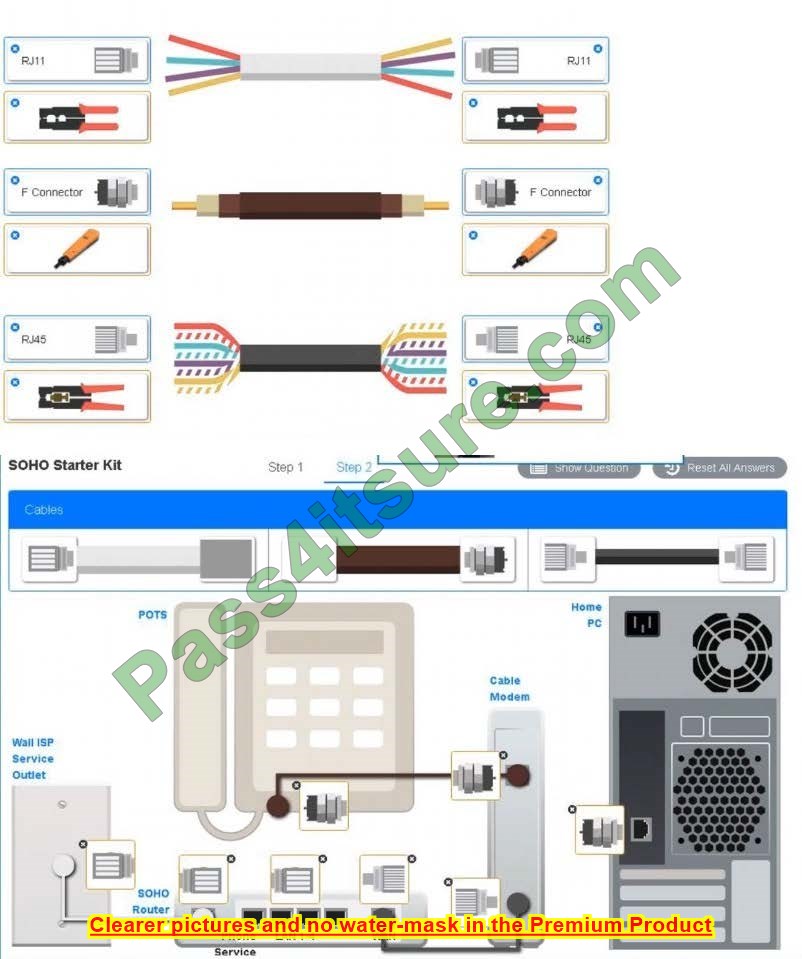
The new N10-008 dumps questions 2024 will help you successfully pass the CompTIA Network+ exam.
How to get it is critical. You can download the N10-008 dumps 2024 (PDF or VCE format) here https://www.pass4itsure.com/n10-008.html to prepare for the exam.
Explore the changes in the CompTIA Network++ certification N10-008 exam 2024
There will be several significant changes in 2024 for the CompTIA Network+ certification N10-008 exam relative to 2023, and 2022.
First of all, with the rapid development of network technology, the exam content will focus more on emerging network technologies and solutions, such as SDN, NFV, cloud computing, and the Internet of Things, to reflect the latest trends and requirements of the current industry.
Second, the exam may increase the examination of cybersecurity and privacy protection, emphasizing the importance of cybersecurity awareness and practice.
In addition, the format of the exam may also be adjusted, such as introducing more hands-on sessions such as case studies, simulations, and troubleshooting, to more comprehensively assess candidates’ practical skills and problem-solving skills.
Finally, the difficulty of the exam may be moderately increased to screen out professionals with a truly high level of networking knowledge and skills.
If you’re looking for free CompTIA Network+ N10-008 exam questions, here’s the one for you too.
(Q11-Q20) CompTIA Network+ N10-008 dumps questions for free sharing
Pick up where last time and continue to share the N10-008 dumps questions …
Provider: Pass4itSure
Number of Questions: 15/1059 (Q11-Q25)
Relevant certifications: CompTIA Network+
Question 11:
According to troubleshooting methodology, which of the following should the technician do NEXT after determining the most likely probable cause of an issue?
A. Establish a plan of action to resolve the issue and identify potential effects
B. Verify full system functionality and, if applicable, implement preventive measures
C. Implement the solution or escalate as necessary
D. Test the theory to determine the cause
Correct Answer: D
Question 12:
A company requires a disaster recovery site to have equipment ready to go in the event of a disaster at its main data center. The company does not have the budget to mirror all the live data to the disaster recovery site. Which of the following concepts should the company select?
A. Cold site
B. Hot site
C. Warm site
D. Cloud site
Correct Answer: C
A warm site is a type of disaster recovery site that has equipment ready to go in the event of a disaster at the main data center but does not have live data or applications. A warm site requires some time and effort to restore the data and services from backups, but it is less expensive than a hot site that has live data and applications.
A cold site is a disaster recovery site that has no equipment or data and requires a lot of time and money to set up after a disaster. A cloud site is a disaster recovery site that uses cloud computing resources to provide data and services, but it may have issues with bandwidth, latency, security, and cost. References: https://www.comptia.org/blog/what-is-a-warm-site
Question 13:
A business is using the local cable company to provide Internet access. Which of the following types of cabling will the cable company MOST likely use from the demarcation point back to the central office?
A. Multimode
B. Cat 5e
C. RG-6
D. Cat 6
E. 100BASE-T
Correct Answer: C
RG-6 is a type of coaxial cable that is commonly used by cable companies to provide Internet access from the demarcation point back to the central office. It has a thicker conductor and better shielding than RG-59, which is another type of coaxial cable.
Multimode and Cat 5e are types of fiber optic and twisted pair cables respectively, which are not typically used by cable companies. Cat 6 and 100BASE-T are standards for twisted pair cables, not types of cabling.
Question 14:
A network technician is configuring a new firewall for a company with the necessary access requirements to be allowed through the firewall. Which of the following should be applied as the LAST rule in the firewall?
A. Secure SNMP
B. Port security
C. Implicit deny
D. DHCP snooping
Correct Answer: C
Implicit denial is a firewall rule that blocks all traffic that is not explicitly allowed by other rules. Implicit denial is usually applied as the last rule in the firewall to ensure that only the necessary access requirements are allowed through the firewall
and that any unwanted or malicious traffic is rejected. Implicit denial can also provide a default security policy and a baseline for auditing and logging purposes. Secure SNMP is a protocol that allows network devices to send event messages
to a centralized server or console for logging and analysis. Secure SNMP can be used to monitor and manage the status, performance, and configuration of network devices. Secure SNMP can also help to detect and respond to potential
problems or faults on the network. However, secure SNMP is not a firewall rule; it is a network management protocol.
Port security is a feature that allows a switch to restrict the devices that can connect to a specific port based on their MAC addresses. Port security can help to prevent unauthorized access, spoofing, or MAC flooding attacks on the switch.
However, port security is not a firewall rule; it is a switch feature.
DHCP snooping is a feature that allows a switch to filter DHCP messages and prevent rogue DHCP servers from assigning IP addresses to devices on the network. DHCP snooping can help to prevent IP address conflicts, spoofing, or denial-of-service attacks on the network. However, DHCP snooping is not a firewall rule; it is a switch feature.
Question 15:
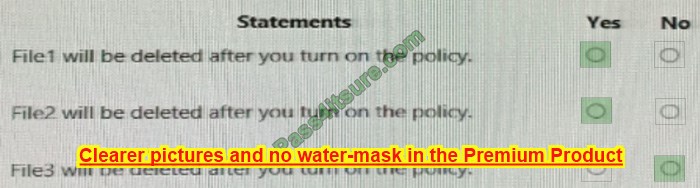
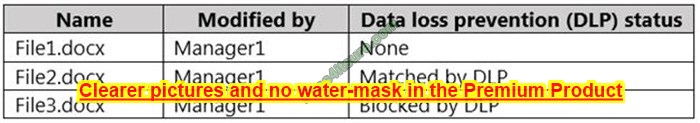
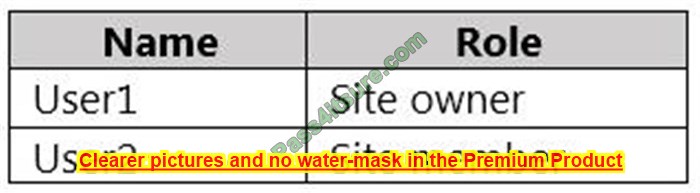
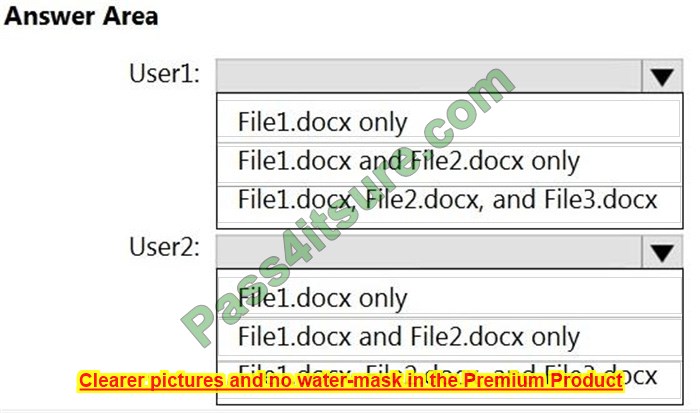
A company rents out a large event space and includes wireless internet access for each tenant. Tenants reserve a two-hour window from the company each week, which includes a tenant-specific SSID. However, all users share the company\’s network hardware.
The network support team is receiving complaints from tenants that some users are unable to connect to the wireless network. Upon investigation, the support team discovers a pattern indicating that after a tenant with a particularly large attendance ends its sessions, tenants throughout the day are unable to connect.
The following settings are common to all network configurations:
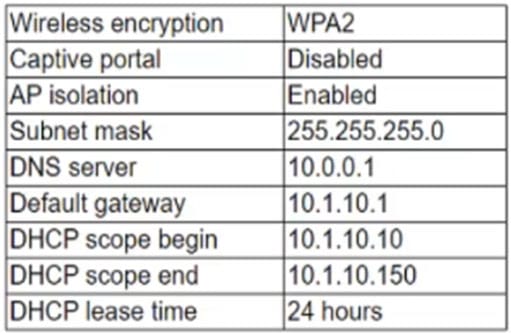
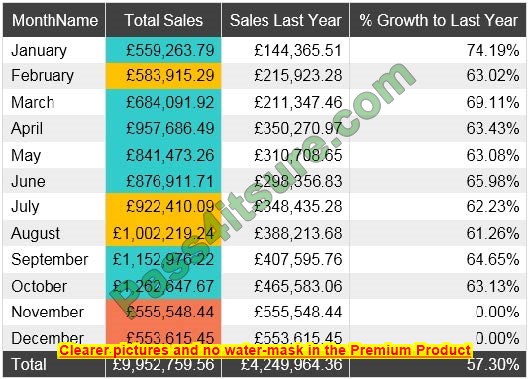
Which of the following actions would MOST likely reduce this Issue? (Select TWO).
A. Change to WPA encryption
B. Change the DNS server to 10.1.10.1.
C. Change the default gateway to 10.0.0.1.
D. Change the DHCP scope end to 10.1.10.250
E. Disable AP isolation
F. Change the subnet mask lo 255.255.255.192.
G. Reduce the DHCP lease time to four hours.
Correct Answer: DG
Question 16:
A technician is troubleshooting intermittent connectivity on a line-of-sight wireless bridge. Which of the following tools should the technician use to determine the cause of the packet loss?
A. Spectrum analyzer
B. OTDR
C. Packet sniffer
D. Multimeter
Correct Answer: A
Question 17:
A technician is troubleshooting a report about network connectivity issues on a workstation. Upon investigation, the technician notes the workstation is showing an APlPA address on the network interface. The technician verifies that the VLAN assignment is correct and that the network interlace has connectivity. Which of the following is MOST likely the issue the workstation is experiencing?
A. DHCP exhaustion
B. A rogue DHCP server
C. A DNS server outage
D. An incorrect subnet mask
Correct Answer: A
APIPA (Automatic Private IP Addressing) is a feature built into Windows operating systems that allows a computer to automatically assign itself an IP address when it is unable to obtain one through DHCP.
When DHCP exhaustion occurs, new clients that attempt to join the network will not be able to obtain an IP address from the DHCP server, and as a result, the computer will use an APIPA address to communicate on the network.
Question 18:
A network manager is configuring switches in IDFs to ensure unauthorized client computers are not connecting to a secure wired network. Which of the following is the network manager MOST likely performing?
A. Disabling unneeded switch ports
B. Changing the default VLAN
C. Configuring DHCP snooping
D. Writing ACLs to prevent access to the switch
Correct Answer: A
The network manager is most likely performing the task of implementing port security on the switches in the Intermediate Distribution Frames (IDFs). Port security is a feature commonly used in network switches to control access to the network by limiting the devices that can connect to individual switch ports.
By configuring port security, the network manager can enforce restrictions on the MAC (Media Access Control) addresses allowed to connect to specific switch ports. This prevents unauthorized client computers or devices from gaining access to the secure wired network.
Typically, the network manager would configure port security to allow only authorized MAC addresses to connect to each switch port. If an unauthorized device attempts to connect, the switch can take actions such as shutting down the port, generating an alert, or applying other security measures to protect the network.
Question 19:
A company\’s users have been reporting excessive latency when connecting to the Internet. The network administration team submitted a change request to upgrade all the obsolete network equipment from 100Mbps to 1Gbps and It was approved. Which of the following documentation types will be needed to measure the success or failure of the upgrade project?
A. Network performance baseline
B. Network configuration documents
C. Equipment Implementation Instructions
D. Inventory management documentation
Correct Answer: A
Question 20:
Which of the following would need to be configured to ensure a device with a specific MAC address is always assigned the same IP address from DHCP?
A. Scope options
B. Reservation
C. Dynamic assignment
D. Exclusion
E. Static assignment
Correct Answer: B
Question 21:
A network engineer configured new Firewalls with the correct configuration to be deployed to each remote branch. Unneeded services were disabled, and all firewall rules were applied successfully. Which of the following should the network engineer perform NEXT to ensure all the firewalls are hardened successfully?
A. Ensure an implicit permit rule is enabled.
B. Configure the log settings on the firewalls to the central syslog server.
C. Update the firewalls with current firmware and software.
D. Use the same complex passwords on all firewalls.
Correct Answer: A
Question 22:
A network administrator walks into a data center and notices an unknown person is following closely. The administrator stops and directs the person to the security desk. Which of the following attacks did the network administrator prevent?
A. Evil twin
B. Tailgating
C. Piggybacking
D. Shoulder surfing
Correct Answer: B
Tailgating represents the situation when an individual without access authorization closely follows an authorized person in a reserved area. The malefactor takes advantage of the moment, when the authorized one opens the door with his badge – and sneaks inside before the door closes.
Piggybacking represents the situation, when someone accesses a reserved area with the permission obtained by deception of an authorized person.
Question 23:
A network technician configures a wireless network that consists of multiple APs for better coverage and allows roaming between the APs. Which of the following types of SSIDs should the technician configure?
A. Basic Service Set
B. Independent Basic Service Set
C. Extended Service Set
D. Distribution System Service
Correct Answer: C
An Extended Service Set (ESS) is a set of interconnected Basic Service Sets (BSS) within a network. It is a network configuration that allows mobile devices to roam seamlessly between different Access Points (APs) within the same network, providing continuous connectivity as the devices move.
Question 24:
A technician is configuring a wireless network and needs to ensure users agree to an AUP before connecting. Which of the following should be implemented to achieve this goal?
A. Captive portal
B. Geofencing
C. Wireless client isolation
D. Role-based access
Correct Answer: A
A captive portal is a web page that is displayed to users before they can access the internet or other network resources. It is commonly used to require users to agree to an Acceptable Use Policy (AUP) before they can connect to a wireless network.
Question 25:
During a risk assessment which of the following should be considered when planning to mitigate high CPU utilization of a firewall?
A. Recovery time objective
B. Uninterruptible power supply
C. NIC teaming
D. Load balancing
Correct Answer: D
The recovery time objective (RTO) is the maximum tolerable length of time that a computer, system, network, or application can be down after a failure or disaster occurs.
Last N10-008 exam questions Q1-Q10.
About the past and present of the CompTIA Network+ exam
The CompTIA Network+ exam was launched in 1999 to validate all knowledge related to network configuration and infrastructure.
Its original version, the N10-007, has now been retired. The latest CompTIA Network+ exam that is also valid is N10-008.
It has up to 90 questions, a mix of performance-based and multiple-choice questions, and requires a passing score of 720 out of 900. Candidates should preferably have a CompTIA A+ certification and a minimum of 9 to 12 months of work experience as a Junior Network Administrator/Network Support Technician.
Times are changing, and so are the exam materials, and the N10-008 exam study resources are the latest, do you have them?
New N10-008 learning materials 2024 integration
(with link)
Book:
- Networking Essentials: A Comptia Network+ N10–008 Textbook
- CompTIA Network+ N10–008 Exam Cram
- CompTIA Network+ N10–008 Cert Guide
Document:
- Network+ (Plus) Certification
- Network+ (N10-008) Certification Study Guide
- Learn online with CertMaster Learn.
- Apply your knowledge with CertMaster Labs
- Practice and prepare for your exam with CertMaster Practice.
You are interested: About N10-008
Is the CompTIA Network+ N10-008 exam more difficult than other entry-level networking certification exams?
Yes, Network+ is more difficult than other entry-level networking certification exams because its focus is vendor-agnostic. Other network certifications may focus on specific hardware or software, while N10-008 is not.
How should I properly study for the N10-008 exam?
Undoubtedly, using CompTIA Network+ N10-008 dumps questions 2024 is the best solution for studying for the exam.
What is the most special thing about the N10-008 exam?
The CompTIA Network+ covers all networks and technologies. Out of all the IT certifications, it is one of the only ones that does not test your hardware or some software details.
In short:
This post is about N10-008 dumps questions 2024 that can help you pass the exam. You need it, and some of the N10-008 exam questions have been shared, which are the latest in 2024.
If you think you can, then go ahead and download the full N10-008 dumps 2024 https://www.pass4itsure.com/n10-008.html (PDF or VCE format) to practice the exam questions and earn your CompTIA Network+ certification.
Thank you for reading, and I wish you all the best.