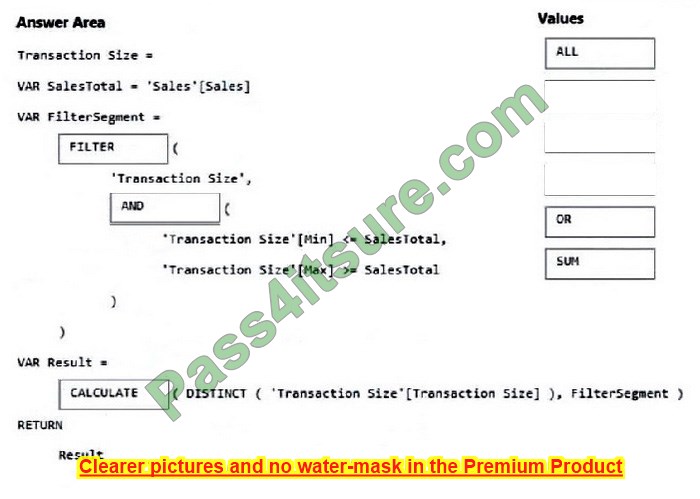
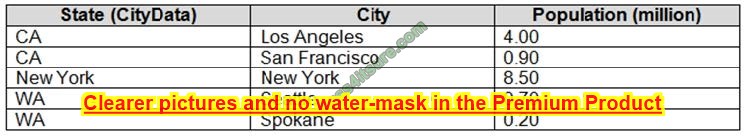
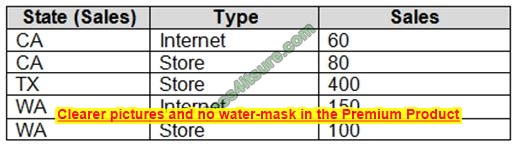
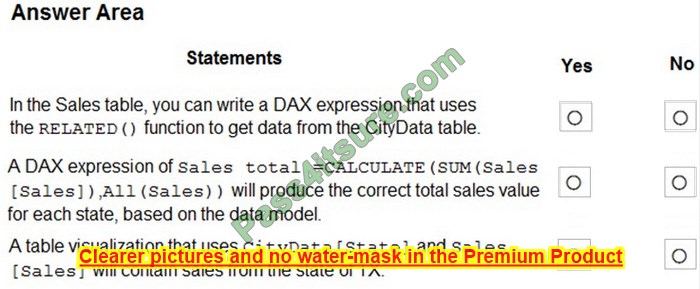
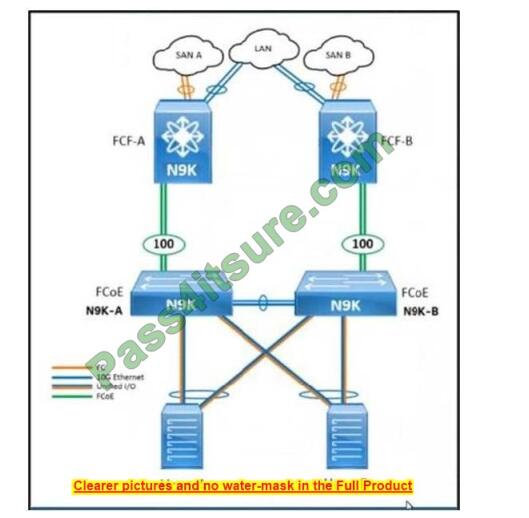
Preparing for the CompTIA Network+ (N10-009) certification exam in 2025? This certificate is a springboard to a career in IT, qualifying you for network management or security-related jobs. But the exam is not easy, and you need reliable resources to help you. This article provides you with free N10-009 practice questions, practical test preparation advice, and trustworthy exam dumps recommendations to help you pass smoothly!
CompTIA N10-009 Exam
N10-009 is a new version of Network+ certification launched in mid-2024, covering five major areas: network foundation, implementation, operation, security and troubleshooting. The exam has a maximum of 90 questions, takes 90 minutes to complete, and has a passing score of 720 points (out of 900 points). The new version focuses on cloud networking, advanced security and wireless technologies and is more challenging than before.
What’s the difficulty? First, knowledge points are updated quickly, such as SD-WAN and cloud security; second, there are many practical questions and time is tight. The good news is, below I’m sharing free resources to help you overcome these obstacles.
Free 2025 N10-009 Practice Questions
| Number of exam questions | Compare |
| 15 | N10-008 |
Question 1:
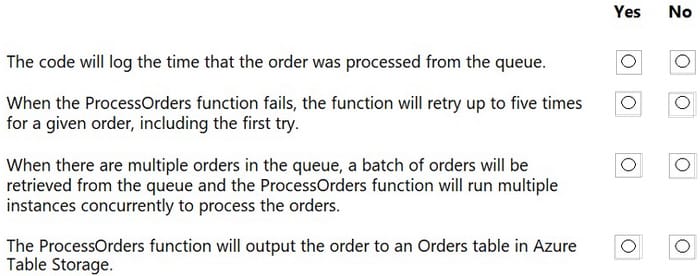
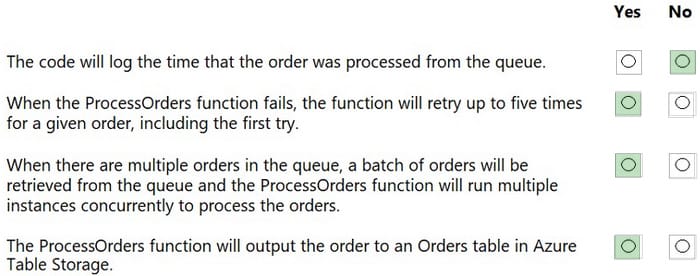
A network administrator replaced a faulty NIC in a printer, but the printer is still not reachable. The printer is configured with the correct IP address, mask, and gateway, and a link light is lit on the switch port that the printer is attached to. Which of the following is the best command for the administrator to run first on the switch?
A. show vlan
B. show route
C. show arp
D. show config
Correct Answer: A
The best command for the administrator to run first on the switch is show vlan, which displays the VLAN configuration information on the switch, such as the VLAN IDs, names, and ports. The show vlan command can help the administrator to verify if the printer is assigned to the correct VLAN, and if there is any mismatch or misconfiguration that prevents the printer from being reachable. The show route command displays the routing table on the switch, which is not relevant for the printer connectivity, as the printer is configured with the correct gateway. The show arp command displays the ARP cache on the switch, which maps the IP addresses to the MAC addresses of the devices. The show arp command can help the administrator to check if the switch has learned the MAC address of the printer, but it is not the best command to run first, as the ARP cache can be cleared or updated frequently. The show config command displays the running configuration on the switch, which includes the VLAN configuration, but it also includes other information that is not related to the printer issue, such as the hostname, the interface settings, the security settings, and so on. The show config command can be overwhelming and time-consuming to analyze, so it is not the best command to run first.
References
1: VLANs and Trunking -N10-008 CompTIA Network+ : 2.3
2: N10-008 CompTIA Network+ : 5.5
3: Interface Configurations -N10-008 CompTIA Network+ : 2.3
4: Configuring VLANs -CompTIA Network+ N10-006 -2.6
Question 2:
A user is having trouble uploading files to a server. However, other users in the department are not experiencing this issue. The network administrator checks the access switch and sees multiple CRC errors on that user\’s switchport. Which of the following should the network administrator do first?
A. Replace the uplink cable for the access switch.
B. Replace the user\’s network cable.
C. Replace the NIC for the user\’s PC.
D. Replace the access switch.
Correct Answer: B
Question 3:
A customer lost the connection to the telephone system. The administration console is configured with multiple network interfaces and is connected to multiple switches. The network administrator troubleshoots and verifies the following:
1.
The support team is able to connect remotely to the administration console.
2.
Rebooting the switch shows solid link and activity lights even on unused ports.
3.
Rebooting the telephone system does not bring the system back online.
4.
The console is able to connect directly to individual modules successfully.
Which of the following is the most likely reason the customer lost the connection?
A. A switch failed.
B. The console software needs to be reinstalled.
C. The cables to the modules need to be replaced.
D. A module failed.
Correct Answer: A
Question 4:
A company wants to implement a disaster recovery site or non-critical applicance, which can tolerance a short period of downltime. Which of the followig type of sites should the company impelement to achive this goal?
A. Hot
B. Cold
C. Warm
D. Passive
Correct Answer: C
A warm site is a compromise between a hot site and a cold site, providing a balance between cost and recovery time. It is partially equipped with the necessary hardware, software, and infrastructure, allowing for a quicker recovery compared to a cold site but at a lower cost than a hot site.
Recovery Time: Warm sites can be operational within hours to a day, making them suitable for non-critical applications that can tolerate short downtimes. Cost-Effectiveness: Warm sites are more economical than hot sites as they do not require all systems to be fully operational at all times.
Network References:
CompTIA Network+ N10-009 Official Certification Guide: Discusses disaster recovery strategies and the different types of recovery sites. Cisco Networking Academy: Provides training on disaster recovery planning and site selection.
Network+ Certification All-in-One uide: Explains the characteristics of hot, warm, and cold sites and their use cases in disaster recovery planning. Warm sites offer a practical solution for maintaining business continuity for non-critical applications, balancing the need for availability with cost considerations.
Question 5:
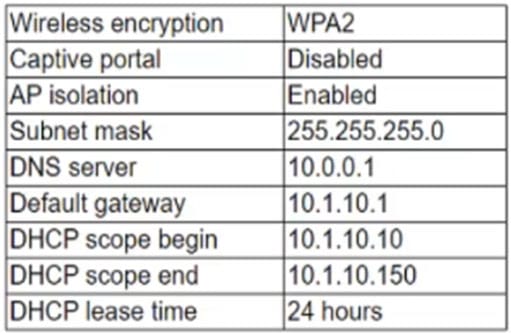
An organization has a guest network with a network IP range of 192.168.1.0/28 using a DHCP pool. One visitor reported difficulties connecting and configured a static IP address. Following this action, another visitor reported intermittent connection issues. Which of the following is the most likely reason?
A. Address pool exhaustion
B. Duplicate IP addresses
C. Misconfigured default gateway
D. Incorrect subnet mask
Correct Answer: B
A duplicate IP address occurs when two devices on the same network have the same IP address assigned to them. This can cause intermittent connection issues, as the network devices may not be able to distinguish between the two conflicting devices. A duplicate IP address can be caused by a visitor manually configuring a static IP address that is already in use by another device on the guest network. The network IP range of 192.168.1.0/28 has only 14 usable host addresses, so the chances of a duplicate IP address are higher than a larger network.
Question 6:
Which of the following network traffic type is sent to all nodes on the network?
A. Unicast
B. Broadcast
C. Multicast
D. Anycast
Correct Answer: B
Broadcast traffic is sent to all nodes on the network. In a broadcast, a single packet is transmitted to all devices in the network segment. This is commonly used for tasks like ARP (Address Resolution Protocol) requests. Broadcast Domain: All devices within the same broadcast domain will receive broadcast traffic.
Network Types: Ethernet networks commonly use broadcast traffic for certain functions, including network discovery and addressing. IPv4 Broadcast: An IPv4 broadcast address (e.g., 255.255.255.255) ensures the packet is sent to all devices on the network.
Network References:
CompTIA Network+ N10-009 Official Certification Guide: Explains network traffic types, including broadcast, unicast, and multicast. Cisco Networking Academy: Provides training on network communication methods and traffic types.
Network+ Certification All-in-One uide: Discusses different types of network traffic and their uses in various network scenarios. Broadcast traffic is essential for network operations that require communication with all nodes, such as ARP requests or DHCP discovery messages.
Question 7:
A network engineer is designing a secure communication link between two sites. The entire data stream needs to remain confidential. Which of the following will achieve this goal?
A. GRE
B. IKE
C. ESP D. AH
Correct Answer: C
Definition of ESP (Encapsulating Security Payload):
uk.co.certification.simulator.questionpool.PList@791927b3 Ensuring Confidentiality:
Comparison with Other Protocols:
Implementation:
References:
CompTIA Network+ study materials on IPsec and secure communication protocols.
Question 8:
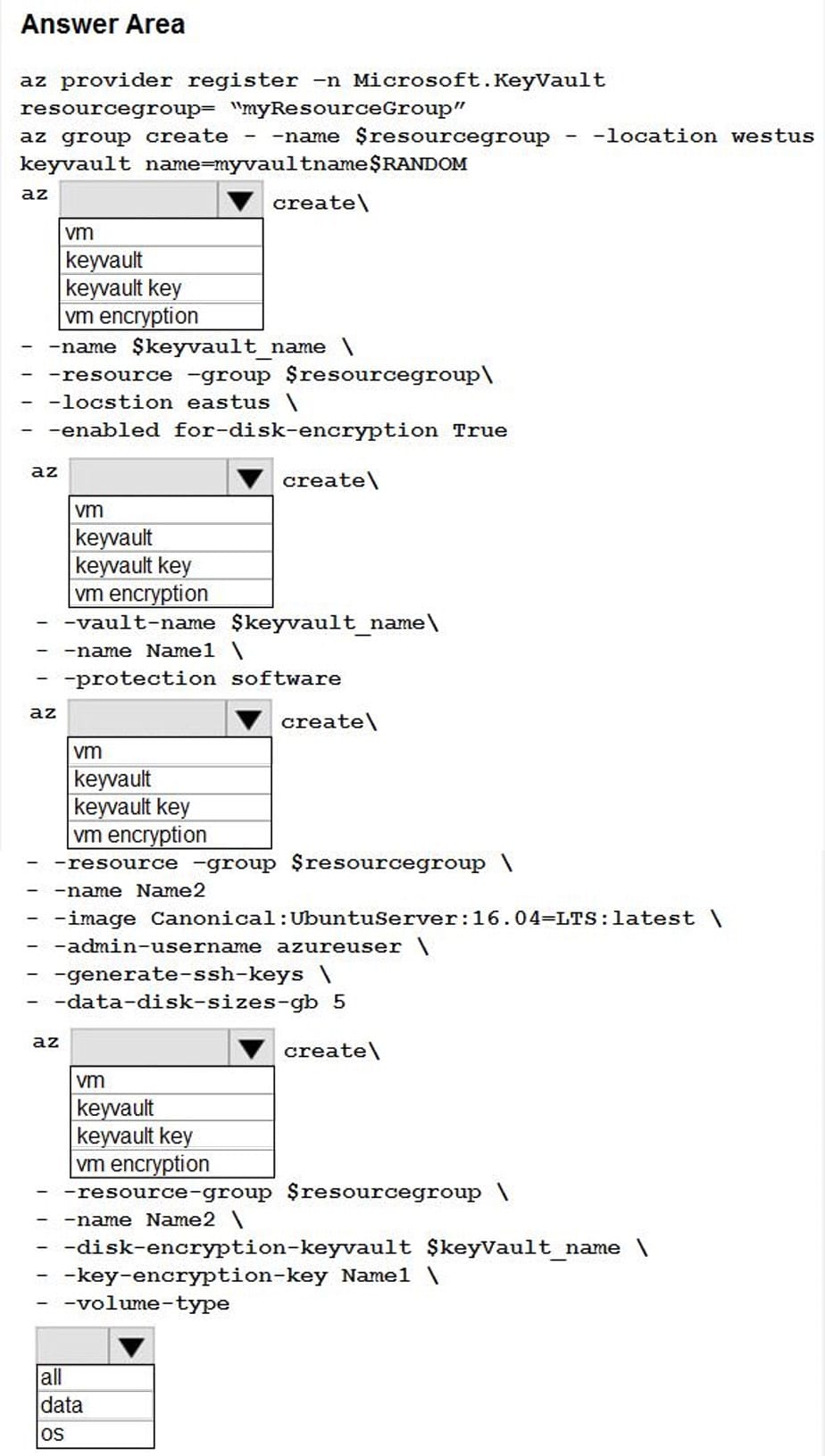
SIMULATION
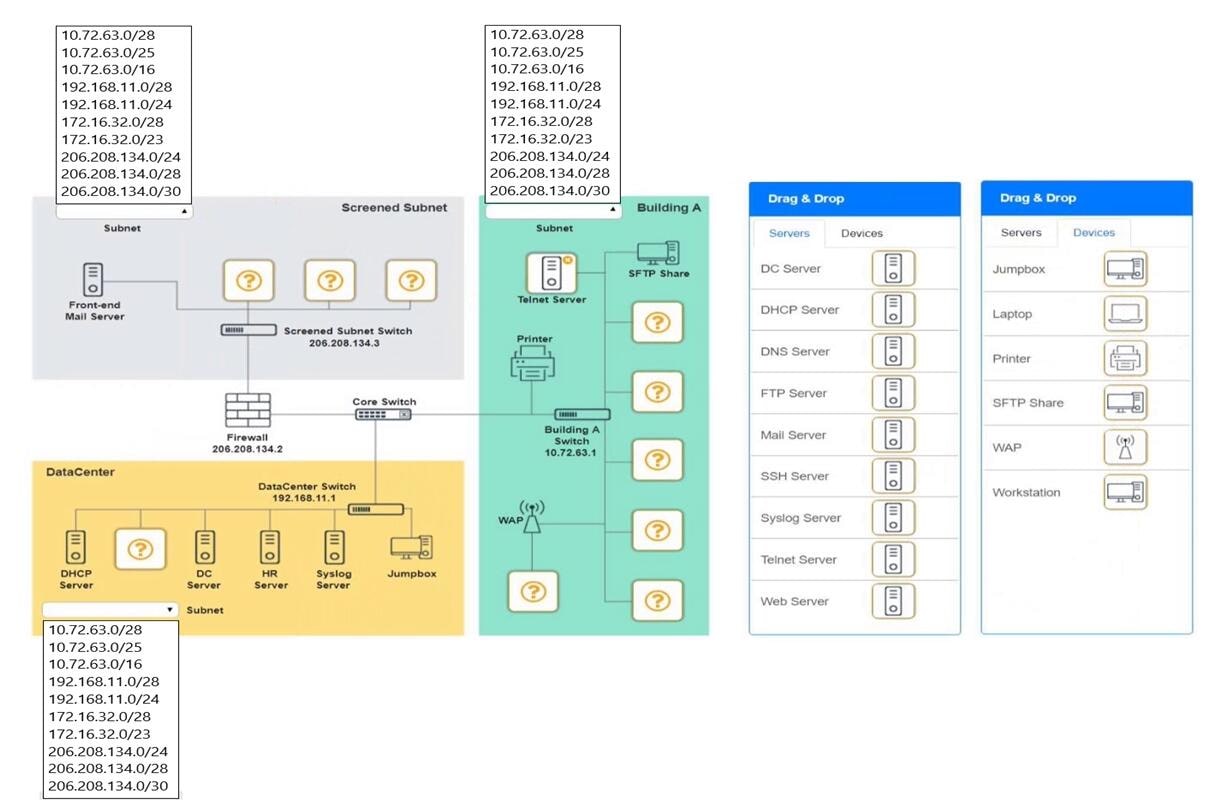
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
Datacenter
– Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
– Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic Building A
–
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
–
Provide devices to support 5 additional different office users
-Add an additional mobile user
-Replace the Telnet server with a more secure solution Screened subnet
– Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
–
Provide a server to handle external 80/443 traffic
–
Provide a server to handle port 20/21 traffic
INSTRUCTIONS
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag and Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A. See explanation below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
Top left subnet – 206.208.134.0/28 Top right subnet – 10.72.63.0/28 Bottom subnet – 192.168.11.0/28
Screened Subnet devices – Web server, FTP server Building A devices – SSH server top left, workstations on all 5 on the right, laptop on bottom left DataCenter devices – DNS server.
Question 9:
Which of the following should a network administrator configure when adding OT devices to an organization\’s architecture?
A. Honeynet
B. Data-at-rest encryption
C. Time-based authentication
D. Network segmentation
Correct Answer: D
Network segmentation involves dividing a network into smaller segments or subnets. This is particularly important when integrating OT (Operational Technology) devices to ensure that these devices are isolated from other parts of the network. Segmentation helps protect the OT devices from potential threats and minimizes the impact of any security incidents. It also helps manage traffic and improves overall network performance.
References:
CompTIA Network+ study materials.
Question 10:
Which of the following is the correct order of components in a bottom-up approach for the three-tier hierarchical model?
A. Access, distribution, and core
B. Core, root, and distribution
C. Core, spine, and leaf
D. Access, core, and roof
Correct Answer: A
The three-tier hierarchical model in network design consists of three layers: access, distribution, and core. The access layer is where devices like PCs and printers connect to the network. The distribution layer aggregates the data received from the access layer switches before it is transmitted to the core layer, which is responsible for high-speed data transfer and routing. This approach improves scalability and performance in larger networks.
References: CompTIA Network+ Exam Objectives and official study guides.
Question 11:
SIMULATION
Users are unable to access files on their department share located on file server 2.
The network administrator has been tasked with validating routing between networks hosting workstation A and file server 2.
INSTRUCTIONS
Click on each router to review output, identify any issues, and configure the appropriate solution.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A. See the solution in Explanation.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
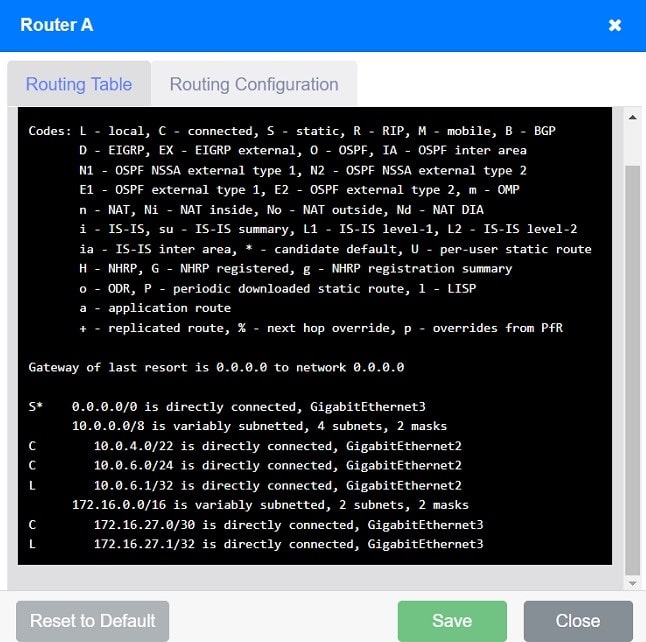
To validate routing between networks hosting Workstation A and File Server 2, follow these steps:
uk.co.certification.simulator.questionpool.PList@713050cf Review Routing Tables:
uk.co.certification.simulator.questionpool.PList@8e0af20 Identify Missing Routes:
Add Static Routes:
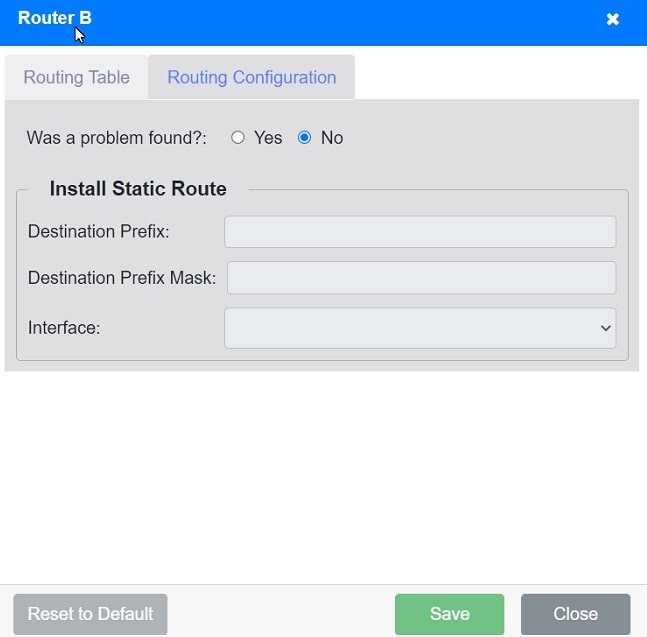
uk.co.certification.simulator.questionpool.PList@783b5def Routing Table:
Gateway of last resort is 0.0.0.0 to network 0.0.0.0 S* 0.0.0.0/0 is directly connected, GigabitEthernet3 10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks C 10.0.4.0/22 is directly connected, GigabitEthernet2 C 10.0.6.0/24 is directly
connected, GigabitEthernet2 L 10.0.6.1/32 is directly connected, GigabitEthernet2 172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks C 172.16.27.0/30 is directly connected, GigabitEthernet3 L 172.16.27.1/32 is directly connected, GigabitEthernet3
uk.co.certification.simulator.questionpool.PList@7b450e21 Routing Table:
Gateway of last resort is 0.0.0.0 to network 0.0.0.0 S* 0.0.0.0/0 is directly connected, GigabitEthernet1 10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks C 10.0.0.0/22 is directly connected, GigabitEthernet1 L 10.0.0.1/32 is directly
connected, GigabitEthernet1 172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks C 172.16.27.4/30 is directly connected, GigabitEthernet1 L 172.16.27.5/32 is directly connected, GigabitEthernet1
uk.co.certification.simulator.questionpool.PList@8809fae Routing Table:
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks S 10.0.0.0/22 via GigabitEthernet1
S 10.0.4.0/22 via GigabitEthernet2
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks C 172.16.27.0/30 is directly connected, GigabitEthernet2 L 172.16.27.2/32 is directly connected, GigabitEthernet2 C 172.16.27.4/30 is directly connected, GigabitEthernet1 L
172.16.27.6/32 is directly connected, GigabitEthernet1
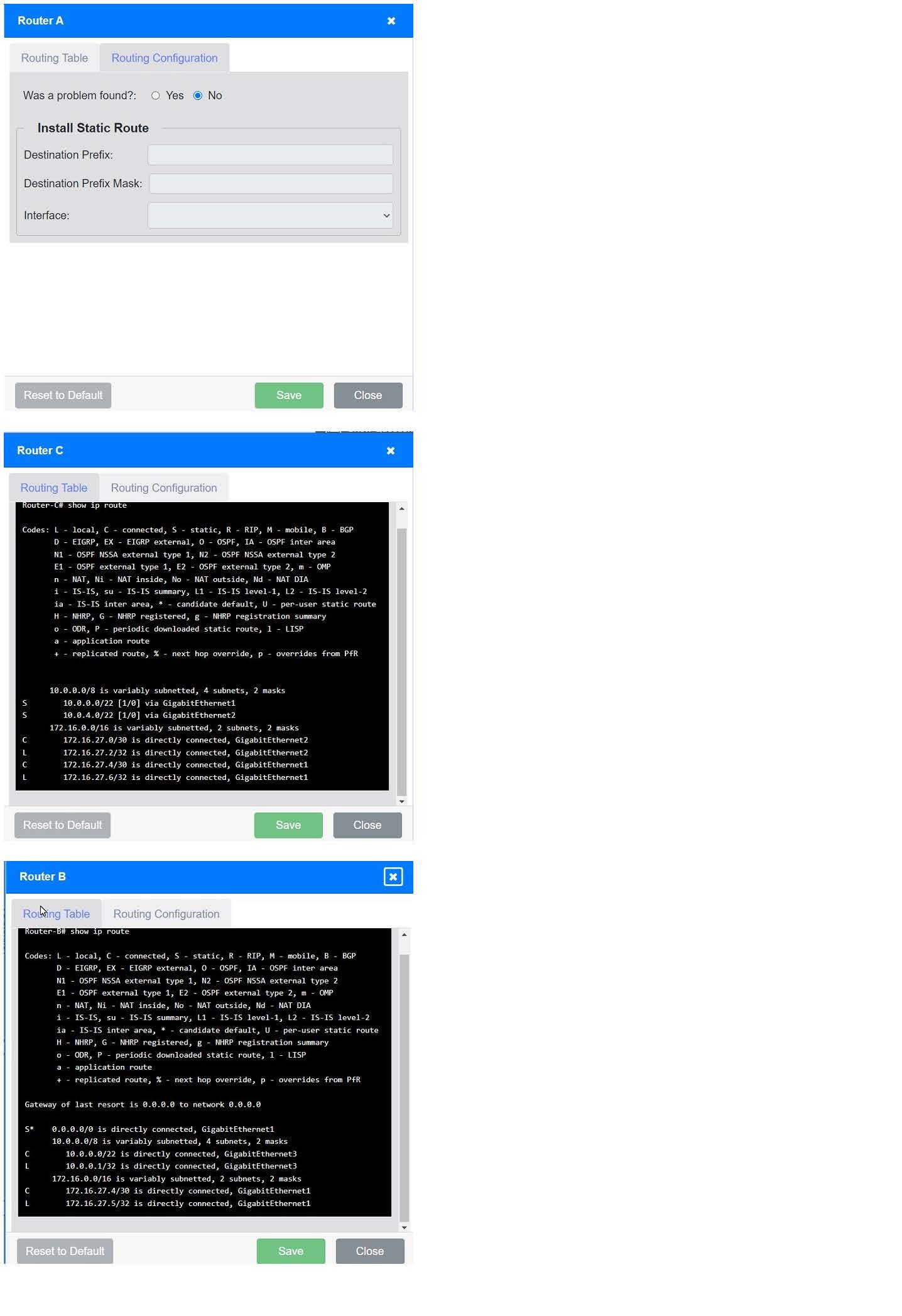
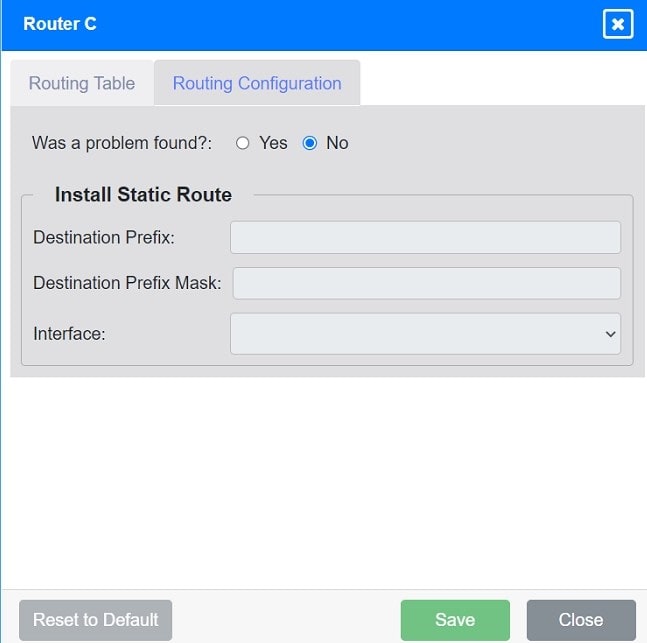
uk.co.certification.simulator.questionpool.PList@594a831 Install Static Route to 10.0.0.0/22 via 172.16.27.1 (assuming Router C\’s IP is 172.16.27.1):
Destination Prefix: 10.0.0.0
Destination Prefix Mask: 255.255.252.0
Interface: GigabitEthernet3
uk.co.certification.simulator.questionpool.PList@27624949 Install Static Route to 10.0.4.0/22 via 172.16.27.5 (assuming Router C\’s IP is 172.16.27.5):
Destination Prefix: 10.0.4.0
Destination Prefix Mask: 255.255.252.0
Interface: GigabitEthernet1
uk.co.certification.simulator.questionpool.PList@74056f82 Install Static Route to 10.0.6.0/24 via 172.16.27.2 (assuming Router A\’s IP is 172.16.27.2):
Destination Prefix: 10.0.6.0
Destination Prefix Mask: 255.255.255.0
Interface: GigabitEthernet2
Install Static Route to 10.0.0.0/22 via 172.16.27.1 (assuming Router B\’s IP is 172.16.27.1):
Destination Prefix: 10.0.0.0
Destination Prefix Mask: 255.255.252.0
Interface: GigabitEthernet1
Summary of Static Routes:
Router A:
uk.co.certification.simulator.questionpool.PList@7874e343 Router B:
Router C:
These configurations ensure that each router knows the correct paths to reach Workstation A and File Server 2, resolving the connectivity issue.
Question 12:
A network administrator\’s device is experiencing severe Wi-Fi interference within the corporate headquarters causing the device to constantly drop off the network. Which of the following is most likely the cause of the issue?
A. Too much wireless reflection
B. Too much wireless absorption
C. Too many wireless repeaters
D. Too many client connections
Correct Answer: A
Reference: CompTIA Network+ Certification Exam Objectives – Wireless Networks section.
Question 13:
Which of the following can also provide a security feature when implemented?
A. NAT
B. BGP
C. FHRP
D. EIGRP
Correct Answer: A
NAT (Network Address Translation) helps hide internal IP addresses from external networks, adding a layer of security by preventing direct access to internal systems from the outside.
Question 14:
A network technician is troubleshooting a web application\’s poor performance. The office has two internet links that share the traffic load.
Which of the following tools should the technician use to determine which link is being used for the web application?
A. netstat
B. nslookup
C. ping
D. tracert
Correct Answer: D
Understanding Tracert:
uk.co.certification.simulator.questionpool.PList@2595382a Determining Traffic Path:
Comparison with Other Tools:
Implementation:
References:
CompTIA Network+ study materials on network troubleshooting and diagnostic tools.
Question 15:
An administrator is configuring a switch that will be placed in an area of the office that is accessible to customers. Which of the following is the best way for the administrator to mitigate unknown devices from connecting to the network?
A. SSE
B. ACL
C. Perimeter network
D. 802.1x
Correct Answer: D
802.1x is a network access control protocol that provides an authentication mechanism to devices trying to connect to a LAN or WLAN. This ensures that only authorized devices can access the network, making it ideal for mitigating the risk of
unknown devices connecting to the network, especially in accessible areas. 802.1x Authentication: Requires devices to authenticate using credentials (e.g., username and password, certificates) before gaining network access. Access
Control: Prevents unauthorized devices from connecting to the network, enhancing security in public or semi-public areas. Implementation: Typically used in conjunction with a RADIUS server to manage authentication requests.
Network References:
CompTIA Network+ N10-009 Official Certification Guide: Covers 802.1x and its role in network security.
Cisco Networking Academy: Provides training on implementing 802.1x for secure network access control.
Network+ Certification All-in-One uide: Explains the benefits and configuration of 802.1x authentication in securing network access.
These questions are close to the actual exam and will help you become familiar with the question types. The more you practice, the more confident you will be!
How to choose reliable N10-009 Exam Dumps
Practice questions lay the foundation, and exam dumps simulate actual combat. However, resources on the market are uneven, so pay attention to the following when purchasing:
Timeliness: Ensure it is the latest version in 2025, covering new content such as cloud security.
Credibility: Choose genuine questions that have been verified by candidates and avoid fake ones.
Diversity: PDF plus VCE simulation software will provide better results.
I recommend Pass4itsure, which has 200+ N10-009 real questions and analysis. It is updated in a timely manner and is cost-effective. Many people rely on it to pass the test. You should try it too! For more information about the exam, you can visit the CompTIA official website.
The first step towards success with N10-009
With free N10-009 practice questions, reliable exam dumps, and exam preparation advice, all you need to do to get certified in 2025 is action. Get started now and visit Pass4itsure for more resources and ace your exam!